On August 2nd at 10:40 pm UTC, a hacker or group of hackers started to exploit multiple SOL users wallets including Slope wallet, Phantom and Trust Wallet. However, the issue is believed to have started with Slope Wallet which enabled other wallets to be compromised. This exploit allowed the hacker/ hackers to drain users wallets completely using at least 4 known wallets.
On the same night, Magic Eden (a prominent NFT platform on Solana) informed users that “there seems to be a widespread SOL exploit at play that’s draining wallets throughout the ecosystem” and informed users to revoke their permissions. This vulnerability has continued to be exploited throughout today culminating in millions lost in SOL and USDC.
Consequences so far
According to Dune analytics, between 7,645 and 9,220 wallets/ accounts have been compromised, although stats from Solscan reveal that 15,234 wallets have been exploited thus far.
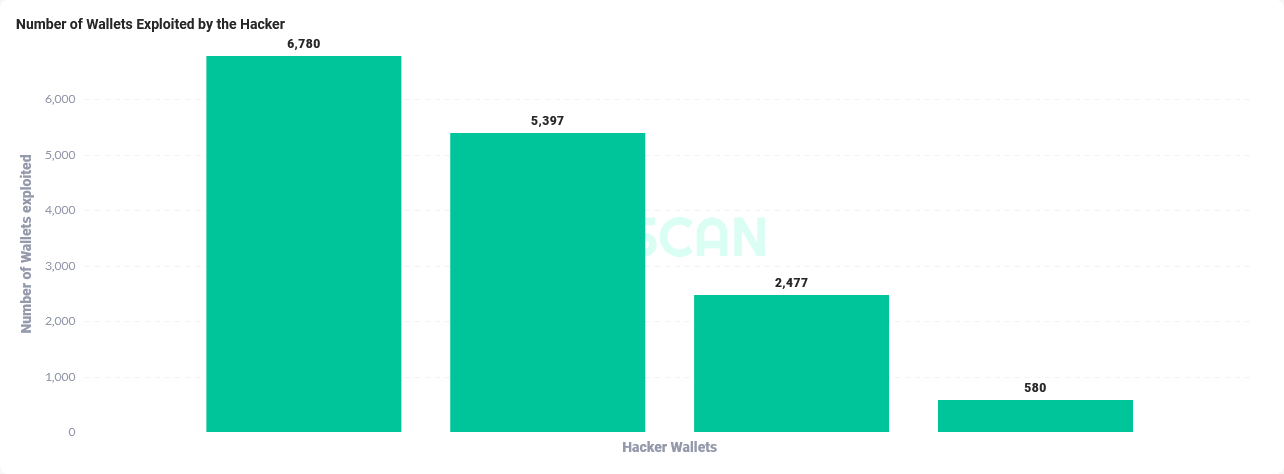
Approximately 41,878 SOL been compromised so far, which is approximately $1,713,257 USD (constantly changing due to the attack and price fluctuations) with a lionshare of the assets residing on what is known as “Hacker wallet 1”.
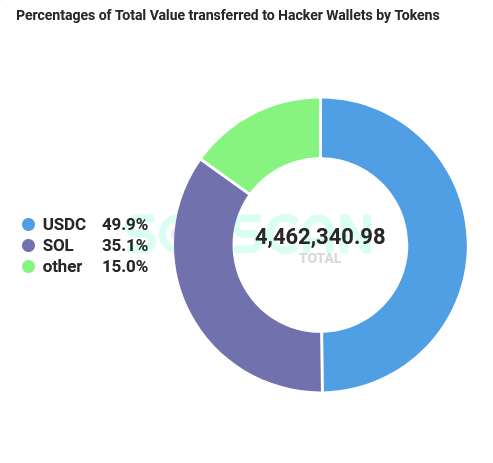
A breakdown from Solscan on the percentages of assets stolen reveals that 49.9% was USDC on Solana, with 35.1% being SOL and with the remaining 15% being other SPL tokens. It is unknown if users are also losing other assets NFTs, although possible.
Timeline and Evidence
In show of solidarity and sleuthery, many key Avalanche figures have speculated on what the cause could be with Avalanche CEO Emin Gun Sirer stating that it could be a “supply chain attack” where a JS library is hacked it exfiltrates (steals) users’ private keys”. The head of engineering at Ava Labs Patrick O’Grady speculated that “I wonder if there’s a nonce reuse bug in some ed25519 signature library solana projects are using”
Buttressing the supply chain theory, Solana Labs CEO Anatoly Yakovenko has stated that “Seems like an iOS supply chain attack. Multiple plausible wallets that only received sol and had no interactions beyond receiving have been affected.” but also later pointed out that Android users were also affected. He also goes on to explain that preponderance of exploited users are used Slope Finance.
Evidence suggests that the Slope Wallet could have “sent plaintext seed phrases to external integration partners.” and the hacks to other wallets have come from imported seed phrases. Many different communities, within and without Solana came together to provide crucial pieces to the larger jigsaw puzzle. Savvy Twitter users have further noted that Slope’s private keys and seed phrases were leaked in plain text, and others were able to reproduce the exploit.
Slope has confirmed that a server-side logging exploit was discovered and has now been removed, but according to Slope’s Twitter “At this moment, 1444 of the 9223 (15%) wallets affected could potentially be traced back to this vulnerability.” This likely means that there are other vulnerabilities and exploits that have been exploited by the hacker/hackers. The root cause of the exploit is still undetermined, even according to Slope Finance although they have now released a Medium article addressing the issue, the actions they’re taking and the actions users should undertake.
An ecosystem wide effort being spearheaded by Solana in tandem with auditors and security incident response teams are still underway to find the root cause.
The importance of cold storage
Users who employ cold storage for their digital assets avoided the aforementioned problems. It is good cybersecurity practice to have a hot wallet where only the necessary funds reside and a cold wallet for long-term safe storage.
Ledger is an industry standard for cryptocurrency security, allowing users to transfer their funds to a hardware wallet securing them in cold storage. With this method you are the custodian of your own digital assets. Ledger is connected to several Web3 service providers making it possible to interact with the space easily and seamlessly while still using their top-tier security. You can perform transactions, interact with NFT’s and even participate in Protocol Staking with your Ledger device.
Another option is to use a custodian to secure your assets. Custodians have institutional grade security in place which come under strict standards for regulations and compliance, they are essentially built to safeguard and insure your digital assets at all costs.
Security and risk mitigations
If you’re using a mobile wallet and want to secure your assets right now,, we believe that all users should do the following in order to stay safe:
1. Go to Settings > Trusted Apps on your wallet
2. Revoke Permissions for all apps
3. Move funds to a cold or hardware wallet
The next step should be to eliminate the risk of getting funds stolen by moving your Solana and SPL tokens to a Ledger hardware wallet. Please follow our comprehensive video tutorial here on how to send your assets safely and securely to a ledger hardware wallet. If you use your ledger do not use the same seed phrase from your hot wallet as it could already be compromised.
Ledger is also engaging in a special, limited-time offer till Sunday where new buyers can get 10% off the Ledger Nano X and Nano S Plus using promo code: MOVESOL2LEDGER


